Threat Watch
Instantly assess your cybersecurity health and gain actionable insights to enhance your protection against threats.
Visit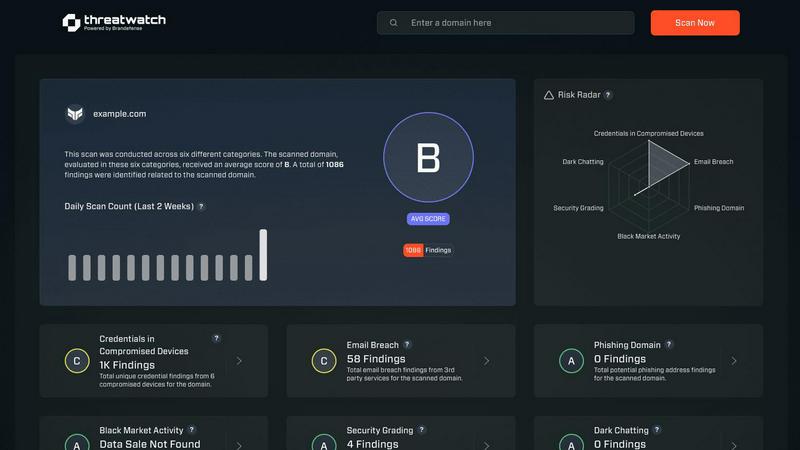
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution designed to safeguard organizations from evolving cyber threats. By leveraging advanced analytics, it evaluates your organization's assets, vulnerabilities, and exposures, providing a comprehensive overview of your cyber health. Ideal for businesses of all sizes, Threat Watch aims to empower security teams with real-time insights that facilitate quicker decision-making and risk mitigation. The platform continuously monitors critical security categories, including compromised devices, breached accounts, phishing addresses, and dark web content. This proactive approach enables organizations to not only identify potential threats but also prioritize and address them with precision. The main value proposition of Threat Watch lies in its ability to streamline cybersecurity efforts, enhancing overall resilience against an increasingly complex threat landscape.
Features of Threat Watch
Real-Time Insights
Threat Watch offers real-time insights into your organization's cybersecurity posture, enabling you to detect vulnerabilities as they arise. This feature ensures that security teams can swiftly respond to emerging threats, reducing the window of opportunity for cyber attackers.
Automated Risk Assessments
With its automated risk assessment capabilities, Threat Watch simplifies the evaluation of potential security threats. Organizations can efficiently analyze their risk landscape without manual intervention, allowing them to focus on strategic security initiatives.
Dark Web Monitoring
This feature continuously scans the dark web for any compromised credentials or sensitive information related to your organization. By identifying potential leaks, Threat Watch helps you take proactive measures to safeguard your assets and maintain customer trust.
Comprehensive Security Evaluation
Threat Watch evaluates multiple critical security categories, providing a holistic view of your organization's security health. This thorough assessment enables organizations to understand their vulnerabilities and prioritize remediation efforts effectively.
Use Cases of Threat Watch
Incident Response
When a security incident occurs, Threat Watch provides invaluable data that aids in incident response efforts. Security teams can quickly identify the source of the breach and take appropriate actions to mitigate damage, ensuring a swift recovery.
Vulnerability Management
Organizations can utilize Threat Watch to continuously monitor their assets for vulnerabilities. By integrating this tool into their vulnerability management processes, security teams can prioritize patching efforts based on the severity of identified risks.
Compliance Reporting
For businesses subject to regulatory compliance, Threat Watch simplifies the reporting process by offering detailed insights into security posture. This feature allows organizations to demonstrate their commitment to cybersecurity and meet compliance requirements more effectively.
Employee Training and Awareness
Threat Watch helps organizations identify areas where employees may be vulnerable to phishing and social engineering attacks. By leveraging this data, companies can tailor their training programs to strengthen employee awareness and reduce the likelihood of successful attacks.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is suitable for organizations of all sizes, from small businesses to large enterprises. Any organization looking to enhance its cybersecurity posture and proactively identify risks can benefit from this solution.
How does Threat Watch ensure data privacy?
Threat Watch prioritizes data privacy by adhering to strict security protocols and industry standards. The platform ensures that sensitive information is protected throughout the monitoring and assessment processes.
Can Threat Watch integrate with existing security tools?
Yes, Threat Watch is designed to integrate seamlessly with various existing security tools and solutions. This interoperability enhances the overall effectiveness of your cybersecurity ecosystem and streamlines workflows.
How often does Threat Watch provide updates on vulnerabilities?
Threat Watch continuously monitors your organization's assets and vulnerabilities, providing updates in real-time. This ensures that you are always informed of the latest threats and can act swiftly to mitigate them.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt streamlines contract management with automated templates, secure signing, and real-time collaboration for teams.
aVenture
aVenture empowers users with AI-driven insights to research private companies, track investments, and analyze market ...